Loading...
UHMC Cybersecurity Networking Session
Debasis Bhattacharya57min
Debasis Bhattacharya (Zoom)
Wait a minute, and then we'll get started, because we are still waiting for McKenna. But
Debasis Bhattacharya (Zoom)
it 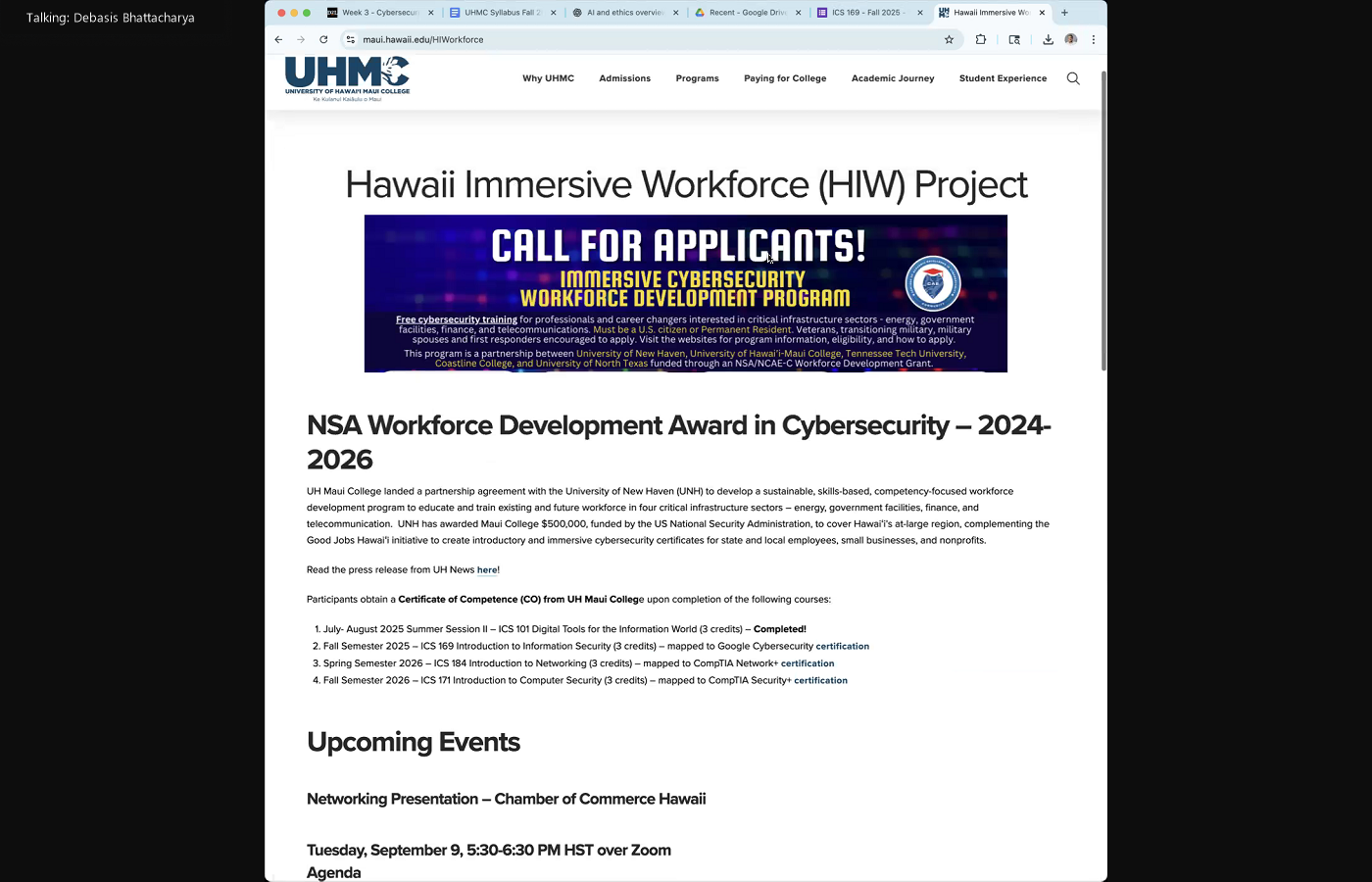
 all right. So welcome everybody again. This is our second networking event we have and, and I think this is a great way for students to get a feel for what is going on in the industry. What is, you know, what, what this project is all about, and maybe ask questions about how things are going and what what's in it for you? So just an overview. This is a project that was fun, that is funded by the NSA and and the and led by University of New Haven and a few other colleges. One of them happens to be coastline Community College in California. The other is Tennessee Tech, Tennessee University of Texas, North Texas, and then UH Maui College. So the idea here is to is to have a cohort of students who, who, who essentially are training in cybersecurity basics or or some details going through the step from last month or last couple of months till the end of next year, which seems like a long time, but actually it goes pretty fast and and the idea of this cohort was not just for you to go through the technologies and content of of
all right. So welcome everybody again. This is our second networking event we have and, and I think this is a great way for students to get a feel for what is going on in the industry. What is, you know, what, what this project is all about, and maybe ask questions about how things are going and what what's in it for you? So just an overview. This is a project that was fun, that is funded by the NSA and and the and led by University of New Haven and a few other colleges. One of them happens to be coastline Community College in California. The other is Tennessee Tech, Tennessee University of Texas, North Texas, and then UH Maui College. So the idea here is to is to have a cohort of students who, who, who essentially are training in cybersecurity basics or or some details going through the step from last month or last couple of months till the end of next year, which seems like a long time, but actually it goes pretty fast and and the idea of this cohort was not just for you to go through the technologies and content of of  cybersecurity, but also to see and get a feel for what the industry is about and how it's how it's evolving and changing. Okay, so what it may be today may not very well be at the end of next year, or some things might be. So that's an overview of the project. Is mostly for Sunny, right? I think most of you students will probably know what you're in already with that said, let me hand it over to our guest. Let's see. So you're here, McKenna, you're here. And ghost, McKenna, you might want to introduce yourself and and then we will you can take it from there. This is the agenda that everybody is aware of.
cybersecurity, but also to see and get a feel for what the industry is about and how it's how it's evolving and changing. Okay, so what it may be today may not very well be at the end of next year, or some things might be. So that's an overview of the project. Is mostly for Sunny, right? I think most of you students will probably know what you're in already with that said, let me hand it over to our guest. Let's see. So you're here, McKenna, you're here. And ghost, McKenna, you might want to introduce yourself and and then we will you can take it from there. This is the agenda that everybody is aware of.
+3


 all right. So welcome everybody again. This is our second networking event we have and, and I think this is a great way for students to get a feel for what is going on in the industry. What is, you know, what, what this project is all about, and maybe ask questions about how things are going and what what's in it for you? So just an overview. This is a project that was fun, that is funded by the NSA and and the and led by University of New Haven and a few other colleges. One of them happens to be coastline Community College in California. The other is Tennessee Tech, Tennessee University of Texas, North Texas, and then UH Maui College. So the idea here is to is to have a cohort of students who, who, who essentially are training in cybersecurity basics or or some details going through the step from last month or last couple of months till the end of next year, which seems like a long time, but actually it goes pretty fast and and the idea of this cohort was not just for you to go through the technologies and content of of
all right. So welcome everybody again. This is our second networking event we have and, and I think this is a great way for students to get a feel for what is going on in the industry. What is, you know, what, what this project is all about, and maybe ask questions about how things are going and what what's in it for you? So just an overview. This is a project that was fun, that is funded by the NSA and and the and led by University of New Haven and a few other colleges. One of them happens to be coastline Community College in California. The other is Tennessee Tech, Tennessee University of Texas, North Texas, and then UH Maui College. So the idea here is to is to have a cohort of students who, who, who essentially are training in cybersecurity basics or or some details going through the step from last month or last couple of months till the end of next year, which seems like a long time, but actually it goes pretty fast and and the idea of this cohort was not just for you to go through the technologies and content of of +1
 cybersecurity, but also to see and get a feel for what the industry is about and how it's how it's evolving and changing. Okay, so what it may be today may not very well be at the end of next year, or some things might be. So that's an overview of the project. Is mostly for Sunny, right? I think most of you students will probably know what you're in already with that said, let me hand it over to our guest. Let's see. So you're here, McKenna, you're here. And ghost, McKenna, you might want to introduce yourself and and then we will you can take it from there. This is the agenda that everybody is aware of.
cybersecurity, but also to see and get a feel for what the industry is about and how it's how it's evolving and changing. Okay, so what it may be today may not very well be at the end of next year, or some things might be. So that's an overview of the project. Is mostly for Sunny, right? I think most of you students will probably know what you're in already with that said, let me hand it over to our guest. Let's see. So you're here, McKenna, you're here. And ghost, McKenna, you might want to introduce yourself and and then we will you can take it from there. This is the agenda that everybody is aware of. McKenna Dale - Chamber of Commerce Hawaii
Hi everyone. My name is McKenna Dale. I am the Associate Director of Workforce Development at the Chamber of Commerce HAWAI'I we sit in a really lovely spot of getting to be the connector and kind of intermediary between industry and training facilities like U, H, CC and other institutions. So super excited to have Sonny and Jon speak with you all today, and I'm excited to learn more. Thanks for having me.
Debasis Bhattacharya (Zoom)
Okay, so I don't think Jon is here, or is he, I mean, oh,
sonny
he's here.
Debasis Bhattacharya (Zoom)
Who's going first? Let me make your co host, and we can go from there. Okay, so Kapu solutions.
Nilo Nono
Jon,
McKenna Dale - Chamber of Commerce Hawaii
oh, Jon, you're muted. Yeah.
Jon Narvaes
All right, I'm here. I'm just trying to get my screen shared. So bear with me.
Debasis Bhattacharya (Zoom)
Yeah, I think you can share your screen now.
Jon Narvaes
All right, just quick confirmation that everybody can see the slide. Okay, great. Good evening. Future workforce of Hawaii from the University of Hawaii, Mali, Maui College, cybersecurity program, special thanks and to Miss Vanessa Rogers for extending the invite to Dr debais Bhattacharya, and also want to send a special acknowledgement for MS McKenna Dale's attendance to this session and to the Chamber of Commerce of HAWAI'I for putting On this outreach event, which we see as extremely valuable to the future workforce. I wanted to also state that this is a discussion, not a lecture. So please, at any time, if you have any questions, please stop me and we'll address those as we go along.
Jon Narvaes
All right, start off with a little background about myself. I am born, raised and educated in HAWAI'I graduate of Roosevelt High School, got my undergraduate at the University of HAWAI'I, Manoa graduate studies at Norwich, but we won't talk about that and its association to the to HAWAI'I. My current role, I am the president and chief technology officer at Kapu solutions, which is a native Hawaiian veteran owned small technology company based here in Honolulu, HAWAI'I. I'm also the co founder of the Pacific technology Cooperation Group, which is an outreach organization that does effectively what we're going to be talking about here today, I'm also a 30 year military veteran. Some of what you see on the slide is some of the different roles and responsibility that I had while in uniform. So this next slide depicts our core capabilities. The big takeaway here is that we are a full service technology solutions provider, and what that means is we do everything from engineering to acquisition of various solutions to providing subject matter expertise, consultation, to service management, and we'll touch a little bit more about that as we kind of flow through the presentation.
Jon Narvaes
So here is some of our credentials. What you'll notice is, with the certifications, we have a number of broad and very specific certifications, broad by way of things like security plus Certified Ethical Hacker, a plus project management, professional, professional to certifications that are more specific, Splunk core, certified user to Cisco certification, amongst other. The same would apply to our partners, we work with both large, general purpose companies and niche partners. So your largest and general purposes would be your Cisco's, your Hewlett Packard's, your Lenovo's, Microsoft Dells, and then more of the niche players would be pep link, which specialized? Specialize in unique edge computing, SD Wan solutions to avoria, which uses Nono technology to provide a two and a half pound display that fits into a headphones case and expands out to 35 inches as far as the customers we deal with, big, small, public and private. So there's a sampling of some of the customers that we work with, a couple that you may recognize off the top, Pearl Harbor, naval shipyard and intermediate maintenance facility Indo Pacific Command. We've also done work as far away as the Kingdom of Saudi Arabia, design and engineering their defense network, to working with local construction companies such as Nan Inc, who you may be familiar with as the prime contractor for the the Hong rail system that's being installed on the island of Oahu, and then our largest customer is the entire federal government, by way of Our recent contract award with the General Service Administration.
Jon Narvaes
Let  little bit more about that Pacific technology cooperation group. The big takeaway here is one of our crown jewels is that we we put on, arguably, what is the largest cybersecurity competition for high schoolers, both private and public, and we're very proud of what that does, by way of greater exposure to cybersecurity, the tools associated With that, and just improving participation in that field. Now, I'm going to dive into what most everybody is interested in, and really here to discuss, I'll start off with the IT commodity areas. And what I want to point out here is that the it commodity areas span a very vast ecosystem of different disciplines that are a part of Information Technology, where a lot of people may only assume or know of a few specializations that make it make up information technology. The reality is, is that there are many everything from someone that's interested in forensics and problem solving to someone that may be more interested into coding and building software applications, someone that may be more interested in physically designing networks. And what I've done is I've highlighted a few of those that I wanted to point out as some key areas that we see at Kapu solutions as high growth areas, Architecting, which is essentially the design and engineer of enterprise networks systems, which would be an encompassing of multiple applications compliance, which is born out of a requirement from the federal government for companies to embrace and comply with security frameworks such as cmmc. We can kind of discuss that if there's any interest there. And then, of course, the elephant in the room, which is AI machine learning and all manner of everything that's associated with that. I'll move on to cybersecurity rules. There's just too vast of an ecosystem to cover everything that cover that falls under the Information Technology umbrella. However, as a core capability within Kapu solutions, that being cybersecurity, we wanted to focus in on that. And there's three that we feel are of particular interest, as kind of stated before, one of the hot commodity areas is AI ml, so data scientists, which are the individuals that curate and train the models, and then the AI ml engineers that actually build the models and take what those data scientists provide to improve the accuracy of the models that they program, and then, of course, the network engineers, which just goes back to the architectural piece that I mentioned
little bit more about that Pacific technology cooperation group. The big takeaway here is one of our crown jewels is that we we put on, arguably, what is the largest cybersecurity competition for high schoolers, both private and public, and we're very proud of what that does, by way of greater exposure to cybersecurity, the tools associated With that, and just improving participation in that field. Now, I'm going to dive into what most everybody is interested in, and really here to discuss, I'll start off with the IT commodity areas. And what I want to point out here is that the it commodity areas span a very vast ecosystem of different disciplines that are a part of Information Technology, where a lot of people may only assume or know of a few specializations that make it make up information technology. The reality is, is that there are many everything from someone that's interested in forensics and problem solving to someone that may be more interested into coding and building software applications, someone that may be more interested in physically designing networks. And what I've done is I've highlighted a few of those that I wanted to point out as some key areas that we see at Kapu solutions as high growth areas, Architecting, which is essentially the design and engineer of enterprise networks systems, which would be an encompassing of multiple applications compliance, which is born out of a requirement from the federal government for companies to embrace and comply with security frameworks such as cmmc. We can kind of discuss that if there's any interest there. And then, of course, the elephant in the room, which is AI machine learning and all manner of everything that's associated with that. I'll move on to cybersecurity rules. There's just too vast of an ecosystem to cover everything that cover that falls under the Information Technology umbrella. However, as a core capability within Kapu solutions, that being cybersecurity, we wanted to focus in on that. And there's three that we feel are of particular interest, as kind of stated before, one of the hot commodity areas is AI ml, so data scientists, which are the individuals that curate and train the models, and then the AI ml engineers that actually build the models and take what those data scientists provide to improve the accuracy of the models that they program, and then, of course, the network engineers, which just goes back to the architectural piece that I mentioned
+1
 little bit more about that Pacific technology cooperation group. The big takeaway here is one of our crown jewels is that we we put on, arguably, what is the largest cybersecurity competition for high schoolers, both private and public, and we're very proud of what that does, by way of greater exposure to cybersecurity, the tools associated With that, and just improving participation in that field. Now, I'm going to dive into what most everybody is interested in, and really here to discuss, I'll start off with the IT commodity areas. And what I want to point out here is that the it commodity areas span a very vast ecosystem of different disciplines that are a part of Information Technology, where a lot of people may only assume or know of a few specializations that make it make up information technology. The reality is, is that there are many everything from someone that's interested in forensics and problem solving to someone that may be more interested into coding and building software applications, someone that may be more interested in physically designing networks. And what I've done is I've highlighted a few of those that I wanted to point out as some key areas that we see at Kapu solutions as high growth areas, Architecting, which is essentially the design and engineer of enterprise networks systems, which would be an encompassing of multiple applications compliance, which is born out of a requirement from the federal government for companies to embrace and comply with security frameworks such as cmmc. We can kind of discuss that if there's any interest there. And then, of course, the elephant in the room, which is AI machine learning and all manner of everything that's associated with that. I'll move on to cybersecurity rules. There's just too vast of an ecosystem to cover everything that cover that falls under the Information Technology umbrella. However, as a core capability within Kapu solutions, that being cybersecurity, we wanted to focus in on that. And there's three that we feel are of particular interest, as kind of stated before, one of the hot commodity areas is AI ml, so data scientists, which are the individuals that curate and train the models, and then the AI ml engineers that actually build the models and take what those data scientists provide to improve the accuracy of the models that they program, and then, of course, the network engineers, which just goes back to the architectural piece that I mentioned
little bit more about that Pacific technology cooperation group. The big takeaway here is one of our crown jewels is that we we put on, arguably, what is the largest cybersecurity competition for high schoolers, both private and public, and we're very proud of what that does, by way of greater exposure to cybersecurity, the tools associated With that, and just improving participation in that field. Now, I'm going to dive into what most everybody is interested in, and really here to discuss, I'll start off with the IT commodity areas. And what I want to point out here is that the it commodity areas span a very vast ecosystem of different disciplines that are a part of Information Technology, where a lot of people may only assume or know of a few specializations that make it make up information technology. The reality is, is that there are many everything from someone that's interested in forensics and problem solving to someone that may be more interested into coding and building software applications, someone that may be more interested in physically designing networks. And what I've done is I've highlighted a few of those that I wanted to point out as some key areas that we see at Kapu solutions as high growth areas, Architecting, which is essentially the design and engineer of enterprise networks systems, which would be an encompassing of multiple applications compliance, which is born out of a requirement from the federal government for companies to embrace and comply with security frameworks such as cmmc. We can kind of discuss that if there's any interest there. And then, of course, the elephant in the room, which is AI machine learning and all manner of everything that's associated with that. I'll move on to cybersecurity rules. There's just too vast of an ecosystem to cover everything that cover that falls under the Information Technology umbrella. However, as a core capability within Kapu solutions, that being cybersecurity, we wanted to focus in on that. And there's three that we feel are of particular interest, as kind of stated before, one of the hot commodity areas is AI ml, so data scientists, which are the individuals that curate and train the models, and then the AI ml engineers that actually build the models and take what those data scientists provide to improve the accuracy of the models that they program, and then, of course, the network engineers, which just goes back to the architectural piece that I mentioned Jon Narvaes
earlier. The next thing I'll jump into is some of the certification paths that you'll see here at capu Solutions and other places of employment. I'll touch on a few of the certification paths. I won't be covering them all again. There's just too many paths that exist. But what I wanted to point out here some some takeaways, which is also germane to the Maui College cybersecurity program, particularly in the government space, is that for anyone that's interested in working for or with the Department of Defense. The core certification required is the Security Plus certification that's to just allow you to touch the network if you are of a administrator. The other takeaway here is, if you look at the information assurance technical, the information assurance management and the information assurance system architecture and engineer. The CISSP is the the highest level certification required to get up to what they would consider as a senior tier for cybersecurity. Then, of course, if you have at the bottom, there's any number of other certifications that you can consider, but the ones to really keep at top of mind would be security plus and CISSP, if you have any desire 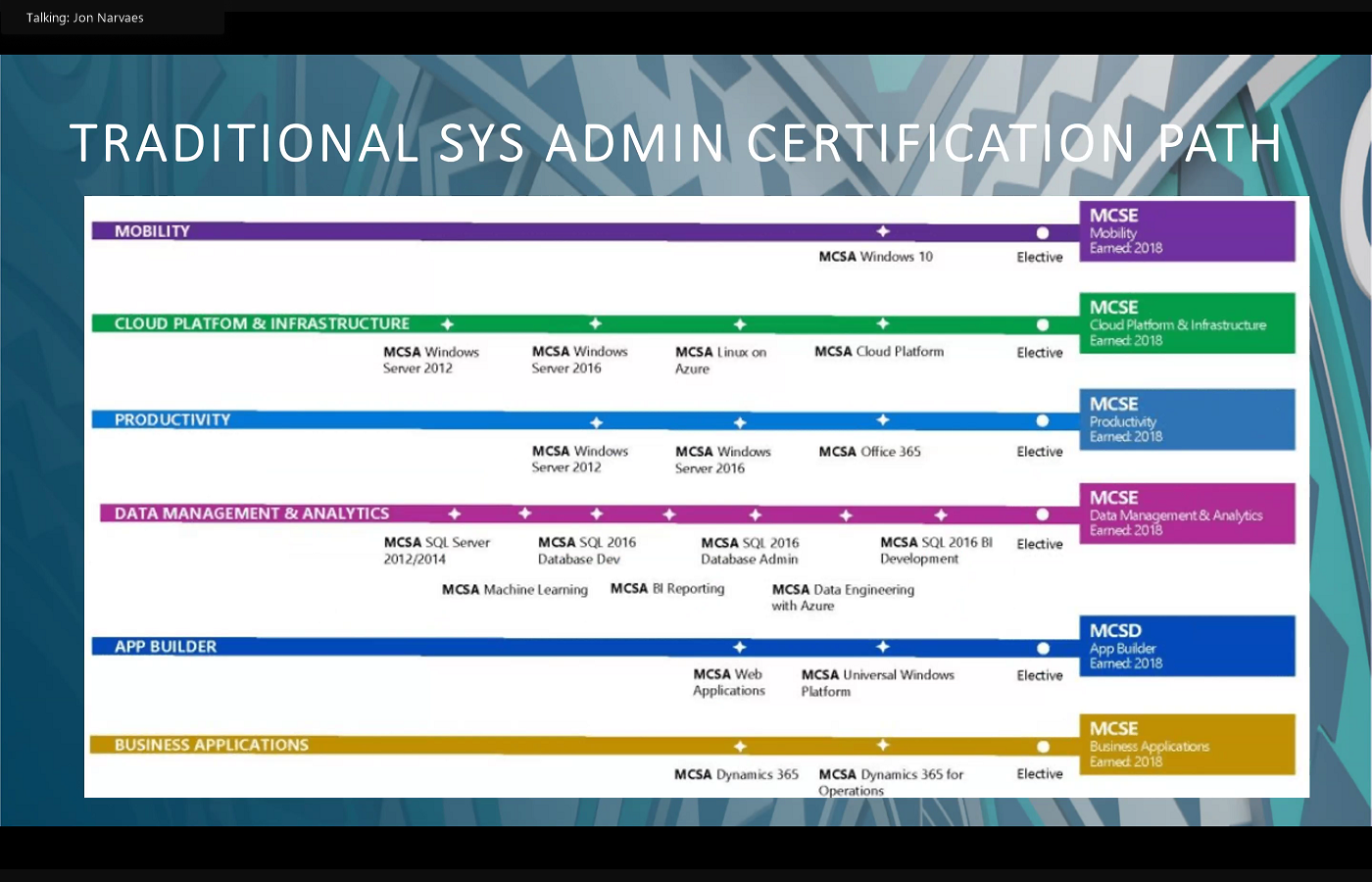
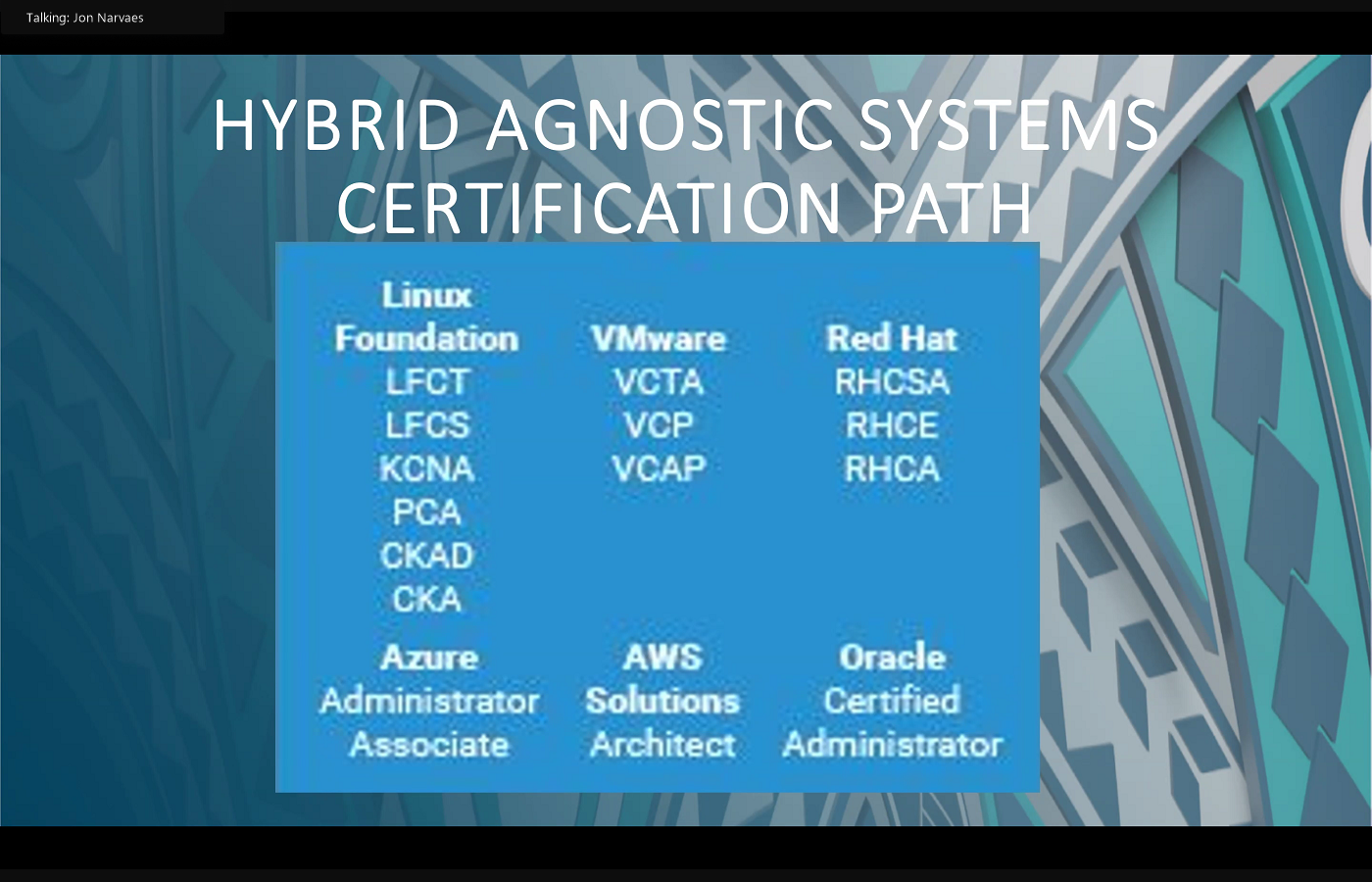 to move into cybersecurity. The next thing I wanted to point out is the traditional network certification paths. I believe myself the doctor, Mr. Rosales. We kind of grew up in an environment where there was really one dominant player in the network architecture business, and the gold standard was the Cisco certifications. So if you became an associate, and you moved into a specialist, and then you eventually got to professional, and eventually leveled up to engineer, then then you were on the glide path to senior expert level network architecture certification. That also applies to system where the vast majority of system administrators would follow a Microsoft path, and that is still applicable in many cases. But what I wanted to point out is that at Kapu solutions and for what we're seeing trend wise is we're no longer in a system where it is not a singular company that dominates. We've kind of moved into an environment where you have something that's agnostic, hybrid, hybrid, being on premise and cloud. And then there's virtualization. There are different operating systems on the server level that you need to be familiar with. That kind of point out Linux as big one. And then also databases, and how we've kind of moved from a SQL Oracle understanding to more of specific database builds. CRM is a big one, so customer relation management, or customer relation management, and then another big one is going to be ERP, which is Enterprise Resource programs. If there's any takeaway from this, it would be that the hybrid environment and those two specialized database programs, if you begin to understand the security implications of running those, those will serve you very well moving in the industry, here's some additional trends that we're seeing. So I won't go too much deeper into the AI ml, but definitely neural network design is top of mind for anyone that's looking at that, including on the security side, as we start to automate a lot of the security analysts, roles that have been traditionally filled by teams of people and are now giving way to systems that are able to simultaneously monitor systems and or sensors and logs across networks, compile that information and provide great threat analysis. Python programming goes hand in hand with the neural network being that that is the program of AI ml. And then I wanted to also point out something that you may not be tracking, which is the layer one lower voltage. And layer one is from the OSI model. The physical layer is what I mean by that, and the number of work, or the large amount of work that comes out of that, to include the physical security side. So not everything is digital. There is a physical security aspect to the field that you guys are currently studying. I've got
to move into cybersecurity. The next thing I wanted to point out is the traditional network certification paths. I believe myself the doctor, Mr. Rosales. We kind of grew up in an environment where there was really one dominant player in the network architecture business, and the gold standard was the Cisco certifications. So if you became an associate, and you moved into a specialist, and then you eventually got to professional, and eventually leveled up to engineer, then then you were on the glide path to senior expert level network architecture certification. That also applies to system where the vast majority of system administrators would follow a Microsoft path, and that is still applicable in many cases. But what I wanted to point out is that at Kapu solutions and for what we're seeing trend wise is we're no longer in a system where it is not a singular company that dominates. We've kind of moved into an environment where you have something that's agnostic, hybrid, hybrid, being on premise and cloud. And then there's virtualization. There are different operating systems on the server level that you need to be familiar with. That kind of point out Linux as big one. And then also databases, and how we've kind of moved from a SQL Oracle understanding to more of specific database builds. CRM is a big one, so customer relation management, or customer relation management, and then another big one is going to be ERP, which is Enterprise Resource programs. If there's any takeaway from this, it would be that the hybrid environment and those two specialized database programs, if you begin to understand the security implications of running those, those will serve you very well moving in the industry, here's some additional trends that we're seeing. So I won't go too much deeper into the AI ml, but definitely neural network design is top of mind for anyone that's looking at that, including on the security side, as we start to automate a lot of the security analysts, roles that have been traditionally filled by teams of people and are now giving way to systems that are able to simultaneously monitor systems and or sensors and logs across networks, compile that information and provide great threat analysis. Python programming goes hand in hand with the neural network being that that is the program of AI ml. And then I wanted to also point out something that you may not be tracking, which is the layer one lower voltage. And layer one is from the OSI model. The physical layer is what I mean by that, and the number of work, or the large amount of work that comes out of that, to include the physical security side. So not everything is digital. There is a physical security aspect to the field that you guys are currently studying. I've got
+2

 to move into cybersecurity. The next thing I wanted to point out is the traditional network certification paths. I believe myself the doctor, Mr. Rosales. We kind of grew up in an environment where there was really one dominant player in the network architecture business, and the gold standard was the Cisco certifications. So if you became an associate, and you moved into a specialist, and then you eventually got to professional, and eventually leveled up to engineer, then then you were on the glide path to senior expert level network architecture certification. That also applies to system where the vast majority of system administrators would follow a Microsoft path, and that is still applicable in many cases. But what I wanted to point out is that at Kapu solutions and for what we're seeing trend wise is we're no longer in a system where it is not a singular company that dominates. We've kind of moved into an environment where you have something that's agnostic, hybrid, hybrid, being on premise and cloud. And then there's virtualization. There are different operating systems on the server level that you need to be familiar with. That kind of point out Linux as big one. And then also databases, and how we've kind of moved from a SQL Oracle understanding to more of specific database builds. CRM is a big one, so customer relation management, or customer relation management, and then another big one is going to be ERP, which is Enterprise Resource programs. If there's any takeaway from this, it would be that the hybrid environment and those two specialized database programs, if you begin to understand the security implications of running those, those will serve you very well moving in the industry, here's some additional trends that we're seeing. So I won't go too much deeper into the AI ml, but definitely neural network design is top of mind for anyone that's looking at that, including on the security side, as we start to automate a lot of the security analysts, roles that have been traditionally filled by teams of people and are now giving way to systems that are able to simultaneously monitor systems and or sensors and logs across networks, compile that information and provide great threat analysis. Python programming goes hand in hand with the neural network being that that is the program of AI ml. And then I wanted to also point out something that you may not be tracking, which is the layer one lower voltage. And layer one is from the OSI model. The physical layer is what I mean by that, and the number of work, or the large amount of work that comes out of that, to include the physical security side. So not everything is digital. There is a physical security aspect to the field that you guys are currently studying. I've got
to move into cybersecurity. The next thing I wanted to point out is the traditional network certification paths. I believe myself the doctor, Mr. Rosales. We kind of grew up in an environment where there was really one dominant player in the network architecture business, and the gold standard was the Cisco certifications. So if you became an associate, and you moved into a specialist, and then you eventually got to professional, and eventually leveled up to engineer, then then you were on the glide path to senior expert level network architecture certification. That also applies to system where the vast majority of system administrators would follow a Microsoft path, and that is still applicable in many cases. But what I wanted to point out is that at Kapu solutions and for what we're seeing trend wise is we're no longer in a system where it is not a singular company that dominates. We've kind of moved into an environment where you have something that's agnostic, hybrid, hybrid, being on premise and cloud. And then there's virtualization. There are different operating systems on the server level that you need to be familiar with. That kind of point out Linux as big one. And then also databases, and how we've kind of moved from a SQL Oracle understanding to more of specific database builds. CRM is a big one, so customer relation management, or customer relation management, and then another big one is going to be ERP, which is Enterprise Resource programs. If there's any takeaway from this, it would be that the hybrid environment and those two specialized database programs, if you begin to understand the security implications of running those, those will serve you very well moving in the industry, here's some additional trends that we're seeing. So I won't go too much deeper into the AI ml, but definitely neural network design is top of mind for anyone that's looking at that, including on the security side, as we start to automate a lot of the security analysts, roles that have been traditionally filled by teams of people and are now giving way to systems that are able to simultaneously monitor systems and or sensors and logs across networks, compile that information and provide great threat analysis. Python programming goes hand in hand with the neural network being that that is the program of AI ml. And then I wanted to also point out something that you may not be tracking, which is the layer one lower voltage. And layer one is from the OSI model. The physical layer is what I mean by that, and the number of work, or the large amount of work that comes out of that, to include the physical security side. So not everything is digital. There is a physical security aspect to the field that you guys are currently studying. I've got Light Maleski
a quick comment on that. I just got back from CEDIA conference in Denver for basically the custom installers and channel. And one of the classes I took was basically the the code writers of the NEC code base want us to stop saying low voltage and start saying limited energy. So that's a that's another trend coming up, basically from the people who kind of monitor and write the NEC chapters seven and eight, which are pertain to low the communications and that kind of things like that.
Jon Narvaes
All right, awesome. So
Jon Narvaes,Light Maleski
limited energy,
Jon Narvaes
yeah, a perfect example of how dynamic this field is not only in the technologies that make it up, but in the lexicon that you have to learn. So it's never it's never ending, and I'll touch more on that when we get to what we look for in applicants.
Light Maleski
Part of that, not moniker, is specifically due to Poe being 48 volts, and some of the states are trying to write their laws, or low voltage is basically 24 volts or less. But there's also another voltage that goes up to 600 volts that can be confused for low voltage. So it's a lot of language in the code there that they're trying to define a little bit better, so that electricians are not pulling your IT infrastructure, but you're actually having specialized, trained people that are handling your ethernet cables and whatnot through the through the infrastructure.
Jon Narvaes
Yeah, makes a lot of sense. And just from being in that industry. In the state of HAWAI'I, at least for state contracts, they do require low voltage licensing. So while industry associations are getting the lexicon to kind of those gears to change, we'd also have to get the the
Jon Narvaes,Light Maleski
politics the licensing board, yep.
Jon Narvaes
Okay, any other questions or comments about that? Okay, last thing on there is GRC. So that stands for governance, risk and compliance, and we see a lot of requirements that are coming out of that by way of government regulation, as I mentioned earlier, and also companies understanding what happens if you don't have good governance on your network, practices that you haven't done due diligence with your risk acceptance, and then the C is embracing some form of security architecture and implementing that across the associated enterprise. This next slide is very briefly succinct what we at Kapu solutions are looking for when a new applicant is applying for any of the positions we have, first one being the foundational understanding. That's what academia is going to provide to you. That's what having certifications will provide, and that's going to be one of the key things we assess to see how much retention, and not just regurgitation of the acronyms and the concepts and the terms, but having understanding on how things work, From my military background, what we would call signal flow, that that's kind of what we're looking for. So is having that understanding of how that entire stack is put together and how the ones and zeros flow within that stack, that that's what we look for. The other thing that we we look at is we look at potential, and that's a big one. Any number of individuals can come in, and we can have them get on a set of network equipment and put that together and or deploy a small or medium network. But if they can't increase or graduate their skills to higher levels, then that that becomes a concern for us. And then the big one for me is we look for people that are lifelong learners, as we kind of touched on earlier this field is extremely dynamic, and in order to stay relevant, in order to know what's coming down the pike, and being able to forecast what your client customer is either going to be asking for, or will need to design production or pipelines, that is an absolute key that we look for in an individual. With that I will submit the balance of time to any questions that anybody has
Debasis Bhattacharya (Zoom)
your quick questions before we go on to Sonny. Anybody? So I have a question for you, Jon, how many, how many people did you hire this summer? New New entrants from college,
Jon Narvaes
new entrance from college. So there's, there's a little bit of, I guess, clarification. So we did bring on four total interns, and we did hire one of those interns this summer. We are looking to ramp up hiring. There's a pretty significant contract that we're working on right now, and we're at least looking to hire at least five individuals by the late spring, or I should say, the late fall, early winter, as to kind of give an idea of what kind of opportunities would be opening up. Great.
Debasis Bhattacharya (Zoom)
Okay, just let you know we have a pause during the summer of 2026 intentionally after network plus and before security plus and I would really like students to get some internship opportunities, even before they learn security, plus, because they'll be in the job market in 2027 spring. So you know, it's great that it's a great to know employers who have internship programs and are willing to host students. Okay? Thank you. Jon, sonny, thank you. You're on
sonny
All right, let me go ahead and share my screen. Jon, can you stop sharing one moment?
Jon Narvaes
Yeah, I think you got it Sonny,
Nathan Withers
okay, you got it, good, good, good, good.
sonny
Set myself up here.
sonny
All right, um, Good evening, guys. My name is son Rosales. I am the president of Ikaika Global Strategic Solutions, just like Jon from Kapu solution. I am a small business local here it and cyber is one of my business lines. I support that heavily here on the islands, not just employment, but also cyber and it education and pipeline build out for workforce development organizations. A little bit about myself, just like Jon, I am a H Army ROTC alumni. We graduated the same program, also a co founder of the Pacific technology cooperation group. He talked a lot about about that we are outreach, and I'm glad he talked about one of our big events that support cybersecurity on the island, cyber forensic five. Oh, also father of three, and definitely embedded here in Hawaii, supporting workforce development opportunities for our young youth here on the island. All right, so Jon went over a lot of requirements for being a cyber professional here in HAWAI'I. I don't want to talk a lot about that because lot of certifications, a lot of acronyms, but I'm gonna talk about the bigger picture. Why is it important Hawaii, and why Hawaii is strategic here in nature, supporting workforce efforts here in the Pacific. Little before I go into that, a little bit my company, I already told you, it, cybersecurity is one of my efforts. A lot of my clients are federal. I support a lot of the defense organizations. My biggest client is United States Army Pacific headquarters out of Ford chapter. I will tell you what I need, and I'll tell you what my customer needs. So my customer is usually what my company needs. Also, I focus on building the workforce here in Hawaii, hiring local talent here and building that structure here. There's a need for that. I would say understanding the operational workforce environment here in Hawaii is quite different in the mainland versus working in Virginia, California, Texas, and that's what makes us really unique. Also makes us unique is that we have indo PACOM headquarters, the largest combat in command in the Department of Defense or Department of War now, but we we host Navy, Pacific army, Pacific Marine, Pacific Air Force, Pacific and Space Force, including even though United States Coast Guard is not Department of Defense, are also also a unique organizations  Here in terms of supporting national interests and security. So all right, so I already talked about the strategic importance of Hawai'i and why we're located here. I mean, I would say there's over 375 military civilian personnel that operates and supports indo Paco, and about 100 service members and civilians that work here in Hawai'i. That's a lot of a lot of data, a lot of information we have to protect. And as as it keeps on continuing growing the workforce and cyber continues to grow, I would say later on my slides, I'll talk about the Defense Department, defense cyber workforce framework. I think Jon talked about little bit about about it, but I'll talk a little bit more about it, and what's current and what are you looking for workforce and talent in the cyber arena, protecting critical infrastructure and the defense network. Again, I again, why is unique? Because we're Island and resources are limited. Rely on internal resources here to support our critical needs in terms of, you know, cyber threats and defense. Again, our defense network is pretty robust, but there's not enough military and civilian employees to support that, and with the critical infrastructure we have sustained support, it requires requirements to protect information data, and building that workforce is critical. It does not start in just college. It starts, I would say, you know, elementary to middle school and high school level, k 12. And my company is looking in that working with workforce development organizations to build that talent. It's not just college. It starts in the K 12 sector. Career Opportunities. Jon talked about that, you know, entry level med fair positions. I'm going to talk about resourcing, getting you there. You know, internships that I support, a support programs like the DoD SkillBridge. I'm not sure how many veterans here, or veteran students here, my company, and other companies I support, support that and transition from military to civilian in the cyber or IT workforce. Internships are great. You know, whether it's paid for great paid or for grade, it's great to get you in the workforce. Later on, I'm going to talk about an internship program that's with DoD called p3 i which helps students transition, or helps not transition, but helps give them experience. How, how's it Life is life working in DoD's like and you know how that transition from internship to employment works? I don't want to talk about skills and certification. Jon talked about that, but I do want to harp on important soft skills. I mean, we can talk about certification all day, but soft skills is something that a lot of employers are looking at if you're willing to learn and understand the environment, your depth new things and good problem solvers. I would tell you that is a good soft skill to have. Another good soft skill to have is communication skills. Just because you know your technical skills in cybersecurity, you're doing times where you have to communicate your skills to non technical key stakeholders. They must understand what this you know, even though you're technically advanced and skilled, you're non technical stakeholders, like some of your boss and DOD may not understand, so you have to break it down in layman terms. Also, I'm gonna talk about some experience on not only just working real world projects and your internships, but also hands on labs with the community. I you know, working with the community is also a great way to develop skills and soft skills to build on
Here in terms of supporting national interests and security. So all right, so I already talked about the strategic importance of Hawai'i and why we're located here. I mean, I would say there's over 375 military civilian personnel that operates and supports indo Paco, and about 100 service members and civilians that work here in Hawai'i. That's a lot of a lot of data, a lot of information we have to protect. And as as it keeps on continuing growing the workforce and cyber continues to grow, I would say later on my slides, I'll talk about the Defense Department, defense cyber workforce framework. I think Jon talked about little bit about about it, but I'll talk a little bit more about it, and what's current and what are you looking for workforce and talent in the cyber arena, protecting critical infrastructure and the defense network. Again, I again, why is unique? Because we're Island and resources are limited. Rely on internal resources here to support our critical needs in terms of, you know, cyber threats and defense. Again, our defense network is pretty robust, but there's not enough military and civilian employees to support that, and with the critical infrastructure we have sustained support, it requires requirements to protect information data, and building that workforce is critical. It does not start in just college. It starts, I would say, you know, elementary to middle school and high school level, k 12. And my company is looking in that working with workforce development organizations to build that talent. It's not just college. It starts in the K 12 sector. Career Opportunities. Jon talked about that, you know, entry level med fair positions. I'm going to talk about resourcing, getting you there. You know, internships that I support, a support programs like the DoD SkillBridge. I'm not sure how many veterans here, or veteran students here, my company, and other companies I support, support that and transition from military to civilian in the cyber or IT workforce. Internships are great. You know, whether it's paid for great paid or for grade, it's great to get you in the workforce. Later on, I'm going to talk about an internship program that's with DoD called p3 i which helps students transition, or helps not transition, but helps give them experience. How, how's it Life is life working in DoD's like and you know how that transition from internship to employment works? I don't want to talk about skills and certification. Jon talked about that, but I do want to harp on important soft skills. I mean, we can talk about certification all day, but soft skills is something that a lot of employers are looking at if you're willing to learn and understand the environment, your depth new things and good problem solvers. I would tell you that is a good soft skill to have. Another good soft skill to have is communication skills. Just because you know your technical skills in cybersecurity, you're doing times where you have to communicate your skills to non technical key stakeholders. They must understand what this you know, even though you're technically advanced and skilled, you're non technical stakeholders, like some of your boss and DOD may not understand, so you have to break it down in layman terms. Also, I'm gonna talk about some experience on not only just working real world projects and your internships, but also hands on labs with the community. I you know, working with the community is also a great way to develop skills and soft skills to build on  your talent here in the cyber workforce community. Uh, earlier, I talked about what DoD was looking for. So this is the department defense, cyber workforce framework. This has been updated. As you can see, cyber is not, you know, means everything. So they have seven workforce elements that DOD looks for, looking for talent. You know, not just cyber, but it cyberspace, the cyberspace effects, intelligence, cyber safety enablers, software engineers, AI, data. And under those elements, there's 33 specialty areas. And under those is 17 work roles, and I'll show you later on example, what DoD looks for in terms of what tasks and KSAs, knowledge skills and abilities that are tend to look for in building these job descriptions for contractors like me and Jon when they hire folks to support department defense, You can see, this is one of many elements here. I put it because it and cyber, if you don't, you got to have a little bit of IT skills do cyber. But if you look on the cyber skills, you can see that the job description, and this is like a evaluation sheet with DoD looks at, you know, all right, the job script. Put it out there. We're looking for our cybersecurity, cyber defense analyst, okay, which is under their framework code, 511, and ID, and this is their work world definition under the description. There are KSAs that follows that, and when they do hire, well, this is more on pertaining to government employees, not contractors. They look at that as a checklist, and I do as a contractor. He's modeled that as well myself, because if they're going to use this as a reference and checklist evaluation sheet, I use it as well as hiring folks in the cyber it work realm.
your talent here in the cyber workforce community. Uh, earlier, I talked about what DoD was looking for. So this is the department defense, cyber workforce framework. This has been updated. As you can see, cyber is not, you know, means everything. So they have seven workforce elements that DOD looks for, looking for talent. You know, not just cyber, but it cyberspace, the cyberspace effects, intelligence, cyber safety enablers, software engineers, AI, data. And under those elements, there's 33 specialty areas. And under those is 17 work roles, and I'll show you later on example, what DoD looks for in terms of what tasks and KSAs, knowledge skills and abilities that are tend to look for in building these job descriptions for contractors like me and Jon when they hire folks to support department defense, You can see, this is one of many elements here. I put it because it and cyber, if you don't, you got to have a little bit of IT skills do cyber. But if you look on the cyber skills, you can see that the job description, and this is like a evaluation sheet with DoD looks at, you know, all right, the job script. Put it out there. We're looking for our cybersecurity, cyber defense analyst, okay, which is under their framework code, 511, and ID, and this is their work world definition under the description. There are KSAs that follows that, and when they do hire, well, this is more on pertaining to government employees, not contractors. They look at that as a checklist, and I do as a contractor. He's modeled that as well myself, because if they're going to use this as a reference and checklist evaluation sheet, I use it as well as hiring folks in the cyber it work realm.
+1
 Here in terms of supporting national interests and security. So all right, so I already talked about the strategic importance of Hawai'i and why we're located here. I mean, I would say there's over 375 military civilian personnel that operates and supports indo Paco, and about 100 service members and civilians that work here in Hawai'i. That's a lot of a lot of data, a lot of information we have to protect. And as as it keeps on continuing growing the workforce and cyber continues to grow, I would say later on my slides, I'll talk about the Defense Department, defense cyber workforce framework. I think Jon talked about little bit about about it, but I'll talk a little bit more about it, and what's current and what are you looking for workforce and talent in the cyber arena, protecting critical infrastructure and the defense network. Again, I again, why is unique? Because we're Island and resources are limited. Rely on internal resources here to support our critical needs in terms of, you know, cyber threats and defense. Again, our defense network is pretty robust, but there's not enough military and civilian employees to support that, and with the critical infrastructure we have sustained support, it requires requirements to protect information data, and building that workforce is critical. It does not start in just college. It starts, I would say, you know, elementary to middle school and high school level, k 12. And my company is looking in that working with workforce development organizations to build that talent. It's not just college. It starts in the K 12 sector. Career Opportunities. Jon talked about that, you know, entry level med fair positions. I'm going to talk about resourcing, getting you there. You know, internships that I support, a support programs like the DoD SkillBridge. I'm not sure how many veterans here, or veteran students here, my company, and other companies I support, support that and transition from military to civilian in the cyber or IT workforce. Internships are great. You know, whether it's paid for great paid or for grade, it's great to get you in the workforce. Later on, I'm going to talk about an internship program that's with DoD called p3 i which helps students transition, or helps not transition, but helps give them experience. How, how's it Life is life working in DoD's like and you know how that transition from internship to employment works? I don't want to talk about skills and certification. Jon talked about that, but I do want to harp on important soft skills. I mean, we can talk about certification all day, but soft skills is something that a lot of employers are looking at if you're willing to learn and understand the environment, your depth new things and good problem solvers. I would tell you that is a good soft skill to have. Another good soft skill to have is communication skills. Just because you know your technical skills in cybersecurity, you're doing times where you have to communicate your skills to non technical key stakeholders. They must understand what this you know, even though you're technically advanced and skilled, you're non technical stakeholders, like some of your boss and DOD may not understand, so you have to break it down in layman terms. Also, I'm gonna talk about some experience on not only just working real world projects and your internships, but also hands on labs with the community. I you know, working with the community is also a great way to develop skills and soft skills to build on
Here in terms of supporting national interests and security. So all right, so I already talked about the strategic importance of Hawai'i and why we're located here. I mean, I would say there's over 375 military civilian personnel that operates and supports indo Paco, and about 100 service members and civilians that work here in Hawai'i. That's a lot of a lot of data, a lot of information we have to protect. And as as it keeps on continuing growing the workforce and cyber continues to grow, I would say later on my slides, I'll talk about the Defense Department, defense cyber workforce framework. I think Jon talked about little bit about about it, but I'll talk a little bit more about it, and what's current and what are you looking for workforce and talent in the cyber arena, protecting critical infrastructure and the defense network. Again, I again, why is unique? Because we're Island and resources are limited. Rely on internal resources here to support our critical needs in terms of, you know, cyber threats and defense. Again, our defense network is pretty robust, but there's not enough military and civilian employees to support that, and with the critical infrastructure we have sustained support, it requires requirements to protect information data, and building that workforce is critical. It does not start in just college. It starts, I would say, you know, elementary to middle school and high school level, k 12. And my company is looking in that working with workforce development organizations to build that talent. It's not just college. It starts in the K 12 sector. Career Opportunities. Jon talked about that, you know, entry level med fair positions. I'm going to talk about resourcing, getting you there. You know, internships that I support, a support programs like the DoD SkillBridge. I'm not sure how many veterans here, or veteran students here, my company, and other companies I support, support that and transition from military to civilian in the cyber or IT workforce. Internships are great. You know, whether it's paid for great paid or for grade, it's great to get you in the workforce. Later on, I'm going to talk about an internship program that's with DoD called p3 i which helps students transition, or helps not transition, but helps give them experience. How, how's it Life is life working in DoD's like and you know how that transition from internship to employment works? I don't want to talk about skills and certification. Jon talked about that, but I do want to harp on important soft skills. I mean, we can talk about certification all day, but soft skills is something that a lot of employers are looking at if you're willing to learn and understand the environment, your depth new things and good problem solvers. I would tell you that is a good soft skill to have. Another good soft skill to have is communication skills. Just because you know your technical skills in cybersecurity, you're doing times where you have to communicate your skills to non technical key stakeholders. They must understand what this you know, even though you're technically advanced and skilled, you're non technical stakeholders, like some of your boss and DOD may not understand, so you have to break it down in layman terms. Also, I'm gonna talk about some experience on not only just working real world projects and your internships, but also hands on labs with the community. I you know, working with the community is also a great way to develop skills and soft skills to build on +1
 your talent here in the cyber workforce community. Uh, earlier, I talked about what DoD was looking for. So this is the department defense, cyber workforce framework. This has been updated. As you can see, cyber is not, you know, means everything. So they have seven workforce elements that DOD looks for, looking for talent. You know, not just cyber, but it cyberspace, the cyberspace effects, intelligence, cyber safety enablers, software engineers, AI, data. And under those elements, there's 33 specialty areas. And under those is 17 work roles, and I'll show you later on example, what DoD looks for in terms of what tasks and KSAs, knowledge skills and abilities that are tend to look for in building these job descriptions for contractors like me and Jon when they hire folks to support department defense, You can see, this is one of many elements here. I put it because it and cyber, if you don't, you got to have a little bit of IT skills do cyber. But if you look on the cyber skills, you can see that the job description, and this is like a evaluation sheet with DoD looks at, you know, all right, the job script. Put it out there. We're looking for our cybersecurity, cyber defense analyst, okay, which is under their framework code, 511, and ID, and this is their work world definition under the description. There are KSAs that follows that, and when they do hire, well, this is more on pertaining to government employees, not contractors. They look at that as a checklist, and I do as a contractor. He's modeled that as well myself, because if they're going to use this as a reference and checklist evaluation sheet, I use it as well as hiring folks in the cyber it work realm.
your talent here in the cyber workforce community. Uh, earlier, I talked about what DoD was looking for. So this is the department defense, cyber workforce framework. This has been updated. As you can see, cyber is not, you know, means everything. So they have seven workforce elements that DOD looks for, looking for talent. You know, not just cyber, but it cyberspace, the cyberspace effects, intelligence, cyber safety enablers, software engineers, AI, data. And under those elements, there's 33 specialty areas. And under those is 17 work roles, and I'll show you later on example, what DoD looks for in terms of what tasks and KSAs, knowledge skills and abilities that are tend to look for in building these job descriptions for contractors like me and Jon when they hire folks to support department defense, You can see, this is one of many elements here. I put it because it and cyber, if you don't, you got to have a little bit of IT skills do cyber. But if you look on the cyber skills, you can see that the job description, and this is like a evaluation sheet with DoD looks at, you know, all right, the job script. Put it out there. We're looking for our cybersecurity, cyber defense analyst, okay, which is under their framework code, 511, and ID, and this is their work world definition under the description. There are KSAs that follows that, and when they do hire, well, this is more on pertaining to government employees, not contractors. They look at that as a checklist, and I do as a contractor. He's modeled that as well myself, because if they're going to use this as a reference and checklist evaluation sheet, I use it as well as hiring folks in the cyber it work realm. sonny
So get into community involvement with the PTCG. In my company, I support the Air Force and Space Force Association cyber camps. I get my interns and my employees involved. It's a good way to give back to the community. I feel like that, teaching your skills, also helping you build your professional development. With that, we support a lot of schools here that is interested in the cyber workforce. What's great about Air Force, Space Force associates efforts, we got the cyber camps every summer. It's one week, and I bring in students from u h West, Oahu, you h Manoa. We can do it remote to teach kids cybersecurity one on one. And we do have advanced scan. This also builds their communication skills as well their soft skills when they want to do when, when they do employ for working DoD I do support the cyber patron mentor, mentor recruitment. Every school is looking for mentor out there to support their Cyber Patriot team. But again, it's a good way to build the Hawai'i cyber talent pipeline here and giving back to the community and K to 12 here in Hawai'i. Another opportunity here I support is the  Pacific Intel Innovation Initiative. This is mainly focused on college students. We're being going on our third year, and there's not only it cyber, but there's internships in electronic warfare, data science and all other STEM fields out there. But I'm going to talk about it cyber here is that it's a good way to well, all internships is a good way to experience workforce and DOD this summer, we showcase the viceroy Maven internship. These internships, is a internship that requires you have a security clearance, and it helps you. It's a great way to understand how DoD works, and get the opportunity to network and learn new skills. Get mentored by DOD civilians, DoD's contractors and DOD military personnel. It's a great program. It is a paid internship, and our goal is to after internship, seek employment with the DoD organization, also with PT rhy. We do support peripherals. You know, we supported one this year, in February, we did a matchmaking session with a lot of these students. It was a great way to network and get local talent to the Department of Defense, organization to companies for employment. So to wrap things up for global strategic solutions. You know, I'm here to mentor, train and build a pipeline in the STEM area in particular, it and cyber mean a company has access to various platforms that build the pipeline. One, one notable the DoD cyber exchange. That's where I got DoD workplace. DOD cyber workforce framework. I help support certification, and if not, I look for other partners to help support other students that looking for employment mentorship and career growth. That's, that's, that's, that's continuous for my company, you know, if it's not with my company, and, you know, with other partner companies as well, Kapu solutions, MC three, technology, large business like Huntington and in Blue Zone, if it's not work, Ikaika, I see can partner with other companies and see if they're looking interested in looking for potential talent here in the island. All right. So with that said, if you want more information on you know, the cyber camp p3 I here's the information. One of my Help Desk employees will reach out to you, and we can try to resource the internship or a community project that involves high school, middle school cybersecurity projects with that said, Hey, thank you. And any questions, I'll be standing by. Great.
Pacific Intel Innovation Initiative. This is mainly focused on college students. We're being going on our third year, and there's not only it cyber, but there's internships in electronic warfare, data science and all other STEM fields out there. But I'm going to talk about it cyber here is that it's a good way to well, all internships is a good way to experience workforce and DOD this summer, we showcase the viceroy Maven internship. These internships, is a internship that requires you have a security clearance, and it helps you. It's a great way to understand how DoD works, and get the opportunity to network and learn new skills. Get mentored by DOD civilians, DoD's contractors and DOD military personnel. It's a great program. It is a paid internship, and our goal is to after internship, seek employment with the DoD organization, also with PT rhy. We do support peripherals. You know, we supported one this year, in February, we did a matchmaking session with a lot of these students. It was a great way to network and get local talent to the Department of Defense, organization to companies for employment. So to wrap things up for global strategic solutions. You know, I'm here to mentor, train and build a pipeline in the STEM area in particular, it and cyber mean a company has access to various platforms that build the pipeline. One, one notable the DoD cyber exchange. That's where I got DoD workplace. DOD cyber workforce framework. I help support certification, and if not, I look for other partners to help support other students that looking for employment mentorship and career growth. That's, that's, that's, that's continuous for my company, you know, if it's not with my company, and, you know, with other partner companies as well, Kapu solutions, MC three, technology, large business like Huntington and in Blue Zone, if it's not work, Ikaika, I see can partner with other companies and see if they're looking interested in looking for potential talent here in the island. All right. So with that said, if you want more information on you know, the cyber camp p3 I here's the information. One of my Help Desk employees will reach out to you, and we can try to resource the internship or a community project that involves high school, middle school cybersecurity projects with that said, Hey, thank you. And any questions, I'll be standing by. Great.
+1
 Pacific Intel Innovation Initiative. This is mainly focused on college students. We're being going on our third year, and there's not only it cyber, but there's internships in electronic warfare, data science and all other STEM fields out there. But I'm going to talk about it cyber here is that it's a good way to well, all internships is a good way to experience workforce and DOD this summer, we showcase the viceroy Maven internship. These internships, is a internship that requires you have a security clearance, and it helps you. It's a great way to understand how DoD works, and get the opportunity to network and learn new skills. Get mentored by DOD civilians, DoD's contractors and DOD military personnel. It's a great program. It is a paid internship, and our goal is to after internship, seek employment with the DoD organization, also with PT rhy. We do support peripherals. You know, we supported one this year, in February, we did a matchmaking session with a lot of these students. It was a great way to network and get local talent to the Department of Defense, organization to companies for employment. So to wrap things up for global strategic solutions. You know, I'm here to mentor, train and build a pipeline in the STEM area in particular, it and cyber mean a company has access to various platforms that build the pipeline. One, one notable the DoD cyber exchange. That's where I got DoD workplace. DOD cyber workforce framework. I help support certification, and if not, I look for other partners to help support other students that looking for employment mentorship and career growth. That's, that's, that's, that's continuous for my company, you know, if it's not with my company, and, you know, with other partner companies as well, Kapu solutions, MC three, technology, large business like Huntington and in Blue Zone, if it's not work, Ikaika, I see can partner with other companies and see if they're looking interested in looking for potential talent here in the island. All right. So with that said, if you want more information on you know, the cyber camp p3 I here's the information. One of my Help Desk employees will reach out to you, and we can try to resource the internship or a community project that involves high school, middle school cybersecurity projects with that said, Hey, thank you. And any questions, I'll be standing by. Great.
Pacific Intel Innovation Initiative. This is mainly focused on college students. We're being going on our third year, and there's not only it cyber, but there's internships in electronic warfare, data science and all other STEM fields out there. But I'm going to talk about it cyber here is that it's a good way to well, all internships is a good way to experience workforce and DOD this summer, we showcase the viceroy Maven internship. These internships, is a internship that requires you have a security clearance, and it helps you. It's a great way to understand how DoD works, and get the opportunity to network and learn new skills. Get mentored by DOD civilians, DoD's contractors and DOD military personnel. It's a great program. It is a paid internship, and our goal is to after internship, seek employment with the DoD organization, also with PT rhy. We do support peripherals. You know, we supported one this year, in February, we did a matchmaking session with a lot of these students. It was a great way to network and get local talent to the Department of Defense, organization to companies for employment. So to wrap things up for global strategic solutions. You know, I'm here to mentor, train and build a pipeline in the STEM area in particular, it and cyber mean a company has access to various platforms that build the pipeline. One, one notable the DoD cyber exchange. That's where I got DoD workplace. DOD cyber workforce framework. I help support certification, and if not, I look for other partners to help support other students that looking for employment mentorship and career growth. That's, that's, that's, that's continuous for my company, you know, if it's not with my company, and, you know, with other partner companies as well, Kapu solutions, MC three, technology, large business like Huntington and in Blue Zone, if it's not work, Ikaika, I see can partner with other companies and see if they're looking interested in looking for potential talent here in the island. All right. So with that said, if you want more information on you know, the cyber camp p3 I here's the information. One of my Help Desk employees will reach out to you, and we can try to resource the internship or a community project that involves high school, middle school cybersecurity projects with that said, Hey, thank you. And any questions, I'll be standing by. Great. Debasis Bhattacharya (Zoom)
Thank you, sonny. Questions, comments, anybody wants a job with Sonny, no, is there
Nathaniel Fredericks
only one cyber camp on all the islands, or are there multiple cyber camps on different islands?
Debasis Bhattacharya (Zoom)
There are multiple cyber camps, sonny, you need to unmute. I run some of them, but Sonny Can I have?
sonny
Yeah, so there's multiple cyber camps. I support, the Air Force, Space Force Association, cyber camp that's hosted every summer. And that good is in conjunction of the Cyber Patriot competition with the schools. What's great about it's updated every year, and it's sponsored by it's a DoD program, you know, and we always seek in, you know, it's not just teachers, but defense industry teaches it too. And what's great about it, it's a curriculum that is updated every year, and at the end of it, they execute a Cyber Range, a CTF, and there's a standard camp, and there's a dance camp,
Debasis Bhattacharya (Zoom)
so I have encouraged students, though I've not got any takers about cyber clubs and cyber challenges and competitions. So what do? What? What does Sonny and Jon think about cyber competitions?
sonny
We host one every year. You know, with the high school and middle school through the Pacific technology cooperation group, we want to host one for college, which is, we were looking for interest in that. We didn't have a lot of teams that are interested in doing that here locally as part of cybertransfer, though I know you h Manoa, ACM has a Team West Oahu has a team, not sure about HPU, but we're open to establish, you know, a cyber range for college level teams.
Debasis Bhattacharya (Zoom)
Jody, let's stay in sync about this with Jody and other folks. Alanito, Jon and I can we can sync up later. Jon, any comments we'll get to you.
Jon Narvaes
No Sure. So to add on to what Mr. Walt Rosalie shared is the cybersecurity challenges is a great way to get into a sandbox environment or a lab environment and actually demonstrate and test your skills. It's not too often that as a cybersecurity professional, particularly when we start talking about vulnerability scanning exploitation, which would be a part of penetration testing that you're given that opportunity. And just to kind of tee off a little and also expand on what we do with the cyber forensics five. Oh, competition is we. We don't just merely provide a Jeopardy style forum where you're doing cipher text decryption or you're answering concept questions. We literally set up servers that are primed with flags, and we empower competitors with Kali Linux servers to actively do exploits on systems. So what better way to demonstrate that you have those skills, and particularly for myself as a company that does do cybersecurity penetration testing, to come with those credentials that you have actually not only learned in the academic environment what those skills and concepts are, but you've actually had the ability to apply them in a competitive environment.
Debasis Bhattacharya (Zoom)
Okay, so students, please get this message. I'm not going to keep on telling you this, but next semester in the networking class, you can probably start your first competition, either nationwide or in Hawaii. We need a team, so let's get going. Okay, so now it's time for McKenna.
McKenna Dale - Chamber of Commerce Hawaii
Oh, I think Noah still has
Debasis Bhattacharya (Zoom)
CIA. You? Sorry,
Noah Ling
sorry. I just had a quick question because I actually had my local CyberPatriot team, and we're not very experienced, mainly because they're very young, and they lack a lot of the resources and skills they need to compete very well. So if any of the speakers are interested in speaking just virtually, just hopping on a zoom call, and then speaking for them, and giving your input as an industry professional, that I think that'd be great, and that would mean a lot.
sonny
Yes, I know through our PTC general channels, we mentor a American High School cyber paycheck team virtually. So it shouldn't be a problem mentoring in the cyber page team in Maui. Is it?
Debasis Bhattacharya (Zoom)
Maui? Students are all over the state here,
sonny
okay? Or even, you know, mainland,
Debasis Bhattacharya (Zoom)
yeah, yeah. So you have online mentors, and you have in person mentors. I've been a CyberPatriot mentor myself for more than a decade. No, that is good. You can stay in touch with the folks who who come to these events. And, you know, I've posted the LinkedIn, LinkedIn solutions. All right, meghanna, let's go fabulous.
McKenna Dale - Chamber of Commerce Hawaii
All right. Well, I just want to say a huge thank you to Jon and Sonny for volunteering your time to share a little bit about your background more personally, as well as your organization super informative. Also want to say thank you to Debasis Professor Vanessa and all of the students here today for also giving your time and your great questions. What I will be sharing about for the next few minutes is kind of these wraparound services that we at the Chamber provide in the form of an employment boot camp so through the good jobs program, which is a free training program provided through the University of Hawaii Community College System. We offer some career readiness programming. Okay, just started sharing my screen, and we will have two sessions running later this month and early October. So as you think about you know, you just downloaded all this information about, oh my gosh, what a great career I could have. But what are those like stepping stones? Right to get your foot in the door, you need more than just your positive attitude and a lot of technical knowledge. You need an excellent resume, and you need to know how to talk about yourself. So that's kind of what we do at these sessions, they're taking place in the evening, from five to 6pm looks like the off days. I'm not sure exactly what days your horse runs, but they are open to you and anyone else you think may benefit. I will have Professor Bhattacharya send out these links and this flyer so you can retain it and join us on September 29 and then October 8, as well as I do offer like one on one resume review and employment consultation. So if you are kind of stumped on how to write a resume, maybe this is like your first job outside of working in the service industry, or your first job ever, and that's just a bit of a blind spot. I'm super help, happy to help and also provide some of that, like industry advisement, or just things that we hear that kind of go far. You know, some things that Sonny and Jon said today about what they really look for in candidates. But our two sessions will be kind of general career readiness. Kind of prepare you for resume, writing, interviewing, networking, all sorts of things like that. And then our second one will be kind of similar today to the session today, we'll have a staffing agency discuss, kind of what they do, and then we'll have a representative from a local IT company talk about their personal journey and then the pathways at their company as well. All right, and I will put my email in the chat. So please feel free to reach out with any career questions. Vanessa, my colleague and I work really closely with a ton of employers and educators in it. So very well, very well connected and super happy to help with any questions or requests you may have.
Debasis Bhattacharya (Zoom)
We meet on Tuesdays and Thursdays, which is not the days when you have this workshop. So it should be good. And I strongly encourage students to attend. Get your LinkedIn profile, you know, set up first, and then make sure Vanessa is your contact.
McKenna Dale - Chamber of Commerce Hawaii
Yes, for sure, you guys can the links in the on the flyer aren't like you can't book it. So I would just make a calendar reminder for yourself and make sure you add that link so it'll just bring
sonny
you straight to the meeting.
Nathan Withers
Yeah, yeah,
sonny
for students here on online, great. Good Job's Hawai'i's a great program. My interns and my employee actually did that, and it helped them a lot. So I encourage you to do that. I would say to myself, I won't speak for Jon. I'm open to do one on one as well, resumes and mock interviews as well. I did that. I do that a lot with the students here, not on Hawai'i, but also in the mainland. So send my contact in the chat, and I can do one on ones and to help out as well.
McKenna Dale - Chamber of Commerce Hawaii
Thank you so much. Sonny. Well, one thing I wanted to add to when you were talking about the competitions is, you know, something that we hear a lot from employers is that when their folks are going through the interview process, they are required to do some live skill testing, whether that's like going back and forth with the interviewer and kind of this, like technical conversation or being put to solve a task by yourself. So I think that those types of activities are going to be so impactful and so helpful that when you get to the interview, you're very comfortable doing that type of thing.
sonny
Oh, definitely. Good point. I forgot about the practical skill test they employers do that. So yes, good point there. Thanks for putting that out. Yeah, for sure.
Debasis Bhattacharya (Zoom)
Okay, the class has been too quiet. We're just making me a little concerned. Any questions or comments, yeah, anything you'd like to know, anything that the folks who did not touch on Don't feel shy, you cannot be shy in this whole
Nilo Nono
thing. I just want to say real quick, hi to McKenna and Jon. It's been a while since I've seen you folks, it's nice seeing you guys again,
Debasis Bhattacharya (Zoom)
and we can't see you.
Nilo Nono
I'm at work. Thanks,
Noah Ling
Nilo, either
sonny
work. Are you in your car?
McKenna Dale - Chamber of Commerce Hawaii,Nilo Nono
I'm at work.
Debasis Bhattacharya (Zoom)
Okay, well, thanks for joining in any other comments anybody wants to I just
Nathaniel Fredericks
wanted to say we're only in week three. For a majority of us here, there's some skills that need to be built and some confidence that needs to be worked on, and then I think you're going to get a lot more interaction from this cohort. But there's a lot of folks that are just digesting some of the technical things that are coming at us. The JBL or the JB learning labs are pretty deep already, if, if you're coming from a background that isn't technical, so I think a lot of the silence is just digestion of everything that they're seeing here. So I know I'm speaking for a majority of the class here and making a lot of assumptions, but I think that's where we're at,
Debasis Bhattacharya (Zoom)
and that's just fine. That's just fine. A part of the
sonny
skills you got to build on, you know, soft skills are things we look for, too.
Debasis Bhattacharya (Zoom)
And a part of this program that I have every month is not that you're not going to see Sonny and Jon again. You know, hopefully you will interact with them and the Chamber of Commerce as we go along. So, you know, this is an ongoing dialog, and maybe there'll be a lot more interaction in a few months when you when you could handle the fire hose that is coming in any other comments, Nathan, what about you? What do you think Nathan is a co instructor here,
Nathan Withers
former Cisco Certified Instructor, CCNA. Yeah, I've got a CCNA lecture, you know, I taught CCNA and taught network class, which now is Cloud Plus, I think,
Nathan Withers
but, but, yeah, it's, you know it's, it's good teaching.
sonny
I'll put something out there. So be a member of ice Hawai'i chapter, IC ISC square, you know that's, it's a chap nonprofit here. I know Nathan knows who of them, but be a member of the IC squared chapter here in Hawaii, they'll help with your CISSP. They're all there. A lot of them are cyber IT professionals. Students are free. So yeah. So Hawaii, I see ISC square. They have meetings here, at the sandbox. They do it virtually, but they're good way to network with the IT cyber and Information Assurance community.
Debasis Bhattacharya (Zoom)
Yeah, I put the link there. There are also, you know, national clubs and teams that the students can participate and possibly attend cybersecurity conferences that are held in Oahu as well. There are many different ways to learn the field. You know, I would wish, maybe a year from now, some of you guys would do a poster competition in a, you know, in a small conference. And these are all learning exercises outside the classroom. But, you know, as Nathaniel said right now they're just doing the labs that in week three, so you go step by step. Any any other questions, comments before you guys all go and go and get dinner or something more important on this hour, if not. Thank you. Sonny. Jon McKenna and Vanessa is not here for for all this. I think this is very helpful. It was really appreciated that you take your time off, you know, to come and speak to the folks students here. I think that is really appreciated. I think, you know, despite the few comments, I think students are kind of internalizing what you say, and hopefully they will learn, learn from you all, and get back to you. And you know, this would be a good kind of a collaboration. I intentionally made this kind of a long program, starting in summer of this year to the end of next year, so that students are not in a rush to just check out their classes and lab assignments, that they can do these things and also learn about what is going on in the industry. So thank you very much, and I will see the class again next week, and have a good day, and I'll talk to you all later. Bye, thank you.
Jon Narvaes
Thanks for having us. Good luck. Thank you. Thank
Debasis Bhattacharya (Zoom)
you. Appreciate it. Bye.
00:0000:00